Zero Trust and NIS2: advanced protection of digital access and identities
What is Zero Trust Architecture and what role does it play in cybersecurity?
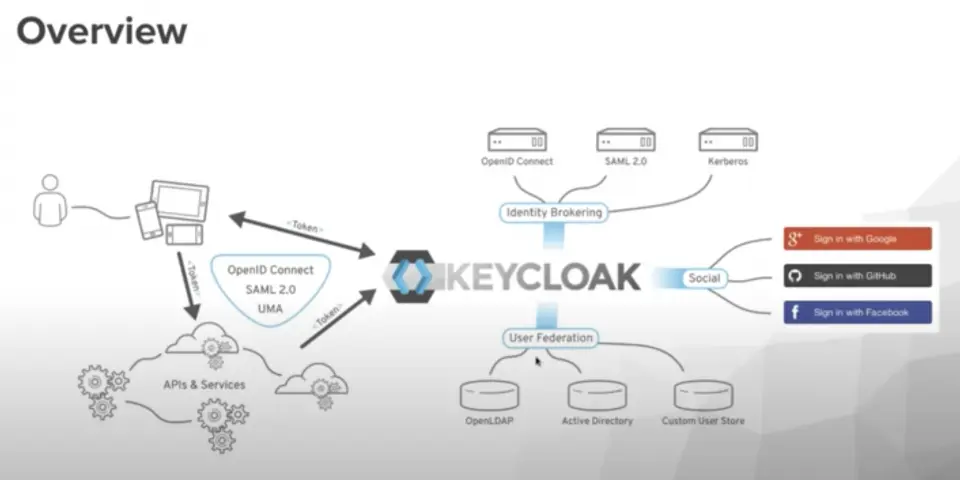
With the term Zero Trust Architecture (ZTA) we indicate a cybersecurity model that, unlike traditional approaches based on the concept of a secure perimeter, does not grant any implicit trust to users or devices within the corporate network.
Within the Zero Trust Architecture, every access is subject to strict authentication and authorization processes, which are based on dynamic criteria capable of analyzing behaviors, evaluating risks, and continuously reviewing the level of trust attributed to the actors involved. In this context, identity management and multi-factor authentication (MFA) represent central elements to ensure effective and continuous control.
How does Zero Trust Architecture help meet the security requirements set by NIS2?
The Zero Trust Architecture takes on a strategic role in the current context, as it represents an effective tool for meeting the requirements of the European NIS2 Directive, aimed at strengthening cybersecurity at the EU level.
In particular, the Zero Trust Architecture aligns perfectly with the objectives of the directive, supporting companies in the implementation of measures related to governance, risk management, incident response, and operational continuity.
This support for the key requirements of NIS2 is achieved through various functionalities:
- Risk assessment and management:
ZTA enables dynamic real-time risk analysis thanks to behavior monitoring, device status, and the application of the principle of least privilege, focusing protection on resources rather than the perimeter. - Response to cyber incidents:
Continuous monitoring and granular access controls allow incidents to be detected and managed quickly and effectively. - Complete visibility:
Detailed logging of user and device activities provides full traceability, supported by SIEM systems for analysis, policy definition, and threat identification. - Operational continuity:
ZTA ensures secure and immediate access to data and applications, even remotely, while maintaining high security standards.
Ready-Made Templates
Is your company subject to NIS2?Visit Yookey’s website to discover the available solutions to ensure compliance.
Visibility and control of digital assets: foundation for Zero Trust and NIS2
Visibility and classification of digital assets are key elements for adopting a Zero Trust model and responding to the requirements of the NIS2 directive.
Although NIS2 does not mandate specific technologies, it requires strategies capable of ensuring a level of security proportional to the risks. In the Zero Trust framework, every resource — from data to devices, from applications to the cloud and even personal endpoints — is considered an asset to be protected and continuously controlled.
To ensure complete visibility of the digital environment, Zero Trust technologies rely on several key tools:
- Identity & Access Management (IAM):
An advanced IAM system, with multi-factor authentication (MFA), is essential to apply solid access control consistent with Zero Trust principles. - Digital Asset Management: Hardware and Software Asset Management solutions (HWAM and SWAM) allow the identification and monitoring of all connected devices, enabling secure configurations and detailed visibility of the infrastructure.
- Security Information and Event Management (SIEM):
SIEM systems aggregate and analyze in real time data on access, traffic, and resources, supporting the continuous adaptation of security policies and the identification of threats. - Principle of Least Privilege:
Access to resources is granted only to the strictly necessary extent and limited in time, reducing the attack surface. - Continuous Authentication: Every access request is subject to constant evaluations, ensuring that authentication and authorization are always updated to the context.
Yookey for NIS2: Secure IAM with Zero Trust Architecture
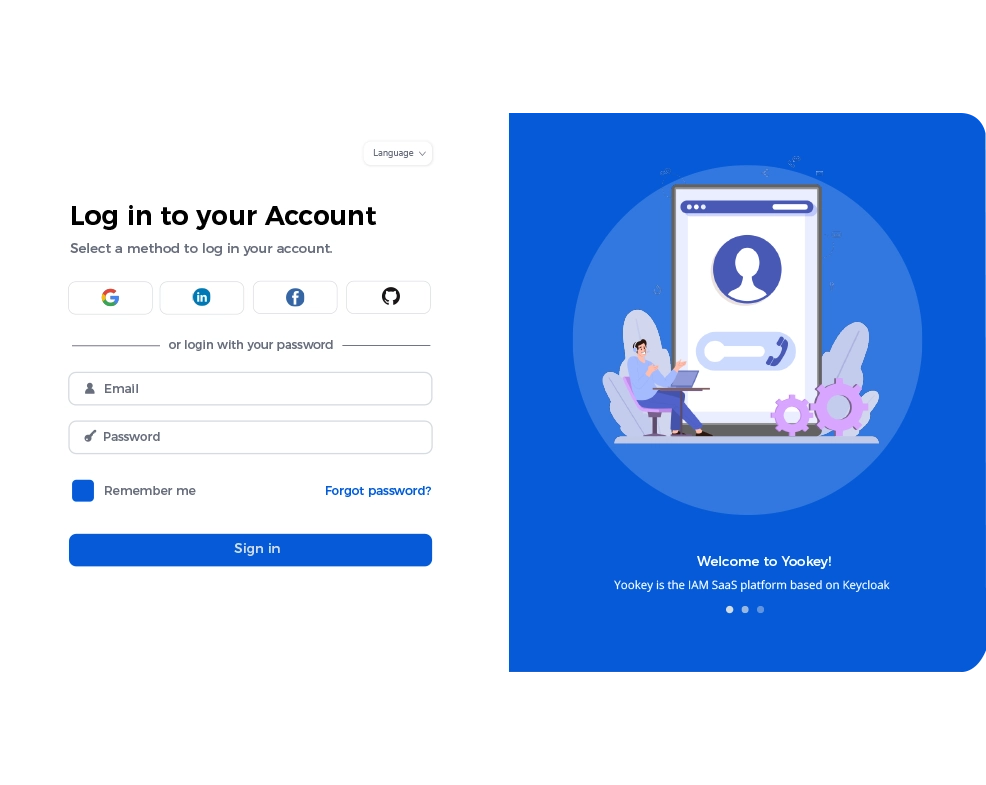
Yookey is an advanced Identity & Access Management (IAM) solution which, through functionalities such as Single Sign-On (SSO) and multi-factor authentication (MFA), enables quick and secure access to all platforms and digital services using a single credential.
Designed according to the principles of the Zero Trust Architecture, Yookey guarantees granular access control and centralized management of digital identities. The platform automates the management of accounts and authorizations, ensuring protected access to critical data and resources, in full compliance with data protection regulations, including the NIS2 Directive.
Speak directly with our team for more information.