IAM Systems and Compliance: Ensuring Adherence to NIS2 and ISO 27001
Why NIS2 and ISO 27001 require an advanced IAM System
To meet the requirements of the NIS2 Directive, Identity and Access Management systems provide advanced solutions for access protection, secure credential management, and continuous monitoring of user activity. Effective identity management helps prevent breaches and ensures that only authorized users can access sensitive data and systems.
The ISO/IEC 27001 standard, an international benchmark for information security, provides a structured framework for implementing an Information Security Management System. Modern IAM systems should support the adoption and maintenance of this standard by integrating controls, processes, and technologies that align with its requirements.
Adopting a robust IAM system enables organizations to protect corporate data and ensure compliance with NIS2 and ISO/IEC 27001. Investing in these technologies is a strategic decision to strengthen the security of digital assets and address the challenges of cybersecurity.
IAM Best Practices for compliance with NIS2 and ISO 27001
- Strong Authentication and Credential Protection: The NIS2 Directive requires the implementation of robust authentication mechanisms, with a strong emphasis on the use of multi-factor authentication (MFA), particularly for privileged accounts and critical resources. Tools such as Public Key Infrastructure (PKI), biometric credentials, and physical or virtual tokens further enhance security. Similarly, ISO 27001 calls for the use of encryption and MFA to protect access to sensitive information.
- Access Control and Privilege Management: Adopting the principle of least privilege is essential to ensure that each user can access only the resources necessary to perform their duties. Role-based access control allows for structured and secure permission management, reducing the attack surface in the event of an account compromise.
- Updated Security Controls: The revised ISO 27001 introduces new controls specifically addressing access management, security during employee onboarding and offboarding, and digital identity administration. The effective implementation of these controls is made possible by deploying robust IAM systems that are well integrated into business processes.
- Traceability and Activity Auditing: An advanced IAM system ensures detailed logging of user activity, enabling complete audit trails. This not only helps detect abnormal behavior but also provides documented evidence of compliance during inspections by relevant authorities.
Ready-Made Templates
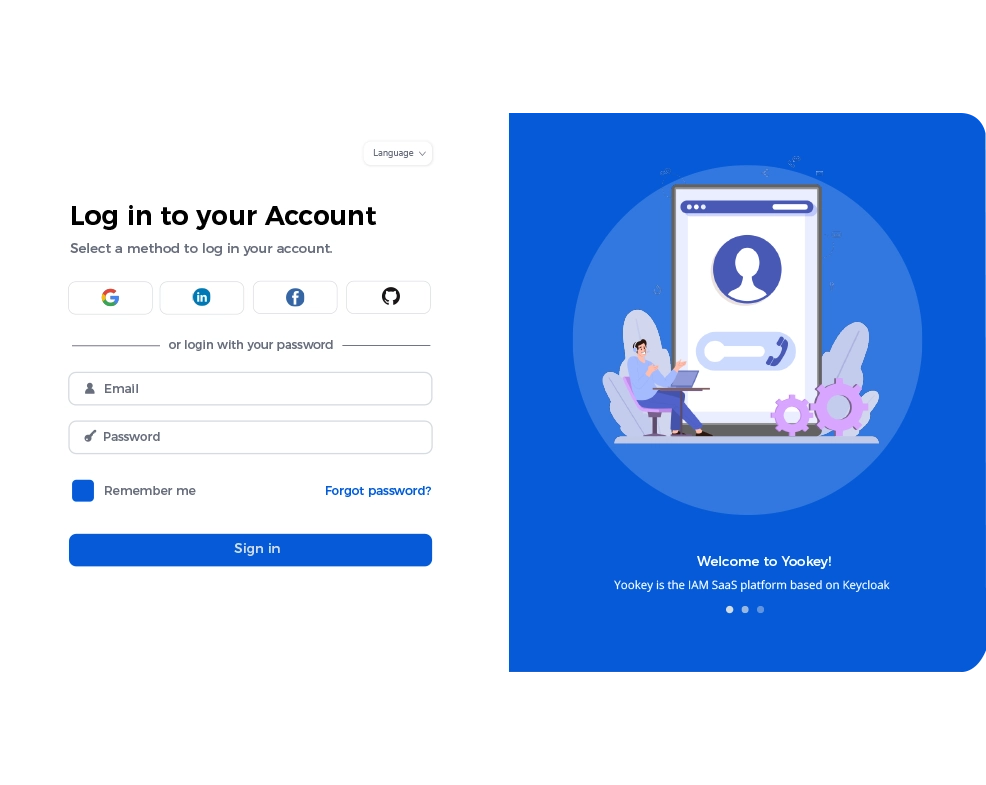
Do you want to learn more?Discover advanced authentication solutions on Yookey
Integrated SSO and compliance
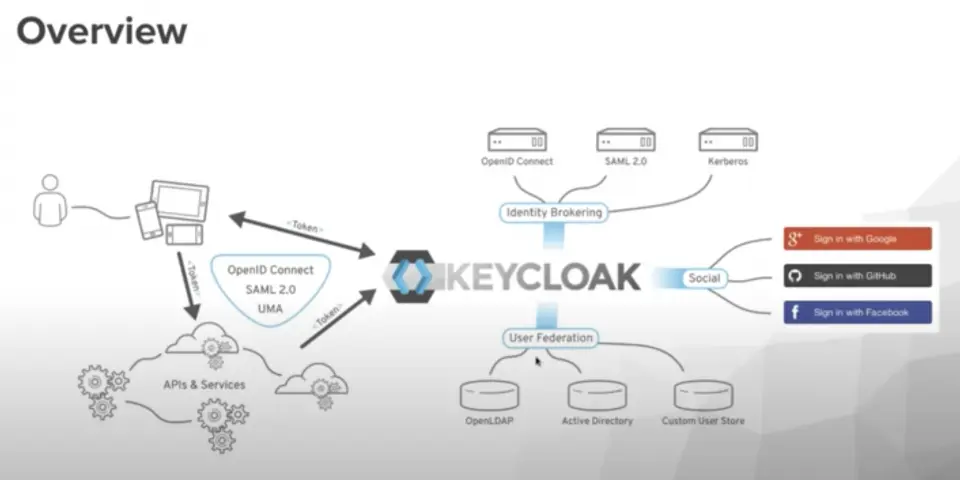
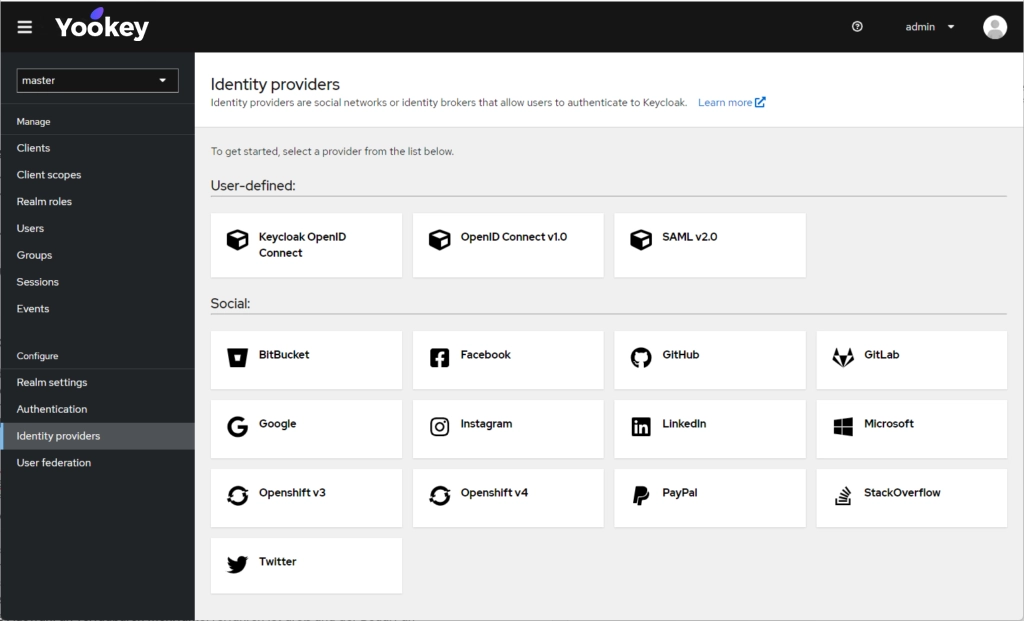
Single Sign-On (SSO) helps ensure regulatory compliance by integrating with Identity and Access Management (IAM) systems. Using protocols like SAML (Security Assertion Markup Language), SSO allows users to access multiple applications with a single set of credentials, simplifying controls and ensuring consistent enforcement of access policies. In this way, SSO facilitates compliance by centralizing access management and supporting auditing and reporting in complex, distributed IT environments.
Yookey IAM System
Yookey’s Identity & Access Management (IAM) system supports compliance with key industry regulations such as NIS2 and ISO 27001 by providing secure, efficient, and customized access to digital resources.
With features like Single Sign-On (SSO) and multi-factor authentication (MFA), Yookey enables businesses and regulated organizations to securely and quickly access all platforms and digital services through a single login. Automated management of accounts and permissions ensures strict control over access to sensitive data and resources, fully complying with privacy regulations.
Speak directly with our team for more information.