Role-Based Access Control (RBAC): What is it, benefits and best practices
What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) constitutes a well-established access management model, which assigns authorizations not to individual users, but to the roles they hold within an organization. In this model, permissions are associated with predefined roles, such as “Administrator,” and users automatically inherit the privileges corresponding to the assigned roles.
This approach allows the focus to shift from individual permission management to organizational function. The RBAC architecture is based on essential components such as Users, Roles, Permissions and Sessions, which operate synergistically to ensure structured and granular control of resources.
What are the benefits of implementing RBAC?
Role-Based Access Control (RBAC) represents one of the most widely used methods to manage user permissions in a structured and sustainable way. Its adoption brings several strategic benefits, in particular:
- Scalability for large organizations: the model is designed to adapt to complex environments with a high number of users and roles.
- Simplification of onboarding and offboarding processes: the assignment or revocation of permissions occurs quickly and efficiently thanks to predefined roles.
- Centralized management of permissions: a single point of control reduces errors and inconsistencies in the distribution of authorizations.
- Increased security: roles limit access only to necessary resources, reducing the attack surface.
- Support for regulatory compliance: the traceability of roles and permissions facilitates audits and adherence to regulations.
Ready-Made Templates
Would you like more information?Visit the Yookey website to discover authentication via SPID and CIE
What does the principle of least privilege mean in RBAC?
The principle of least privilege (PoLP) establishes that each user should receive only the authorizations strictly necessary to perform their duties, thereby limiting access exclusively to essential resources.
The RBAC model fully supports this principle, as permissions are not arbitrarily assigned to individual users but are strictly associated with roles that have defined responsibilities. This approach reduces the attack surface and limits potential damage in the event of an account compromise, since a malicious or negligent user would have access only to a restricted set of resources.
A useful practice to maintain the effectiveness of this model is the periodic review of roles and their corresponding assignments. Continuous monitoring and updates, potentially supported by automated provisioning and de-provisioning processes, prevent users from retaining obsolete privileges after a role or function change.
Access Control with Yookey
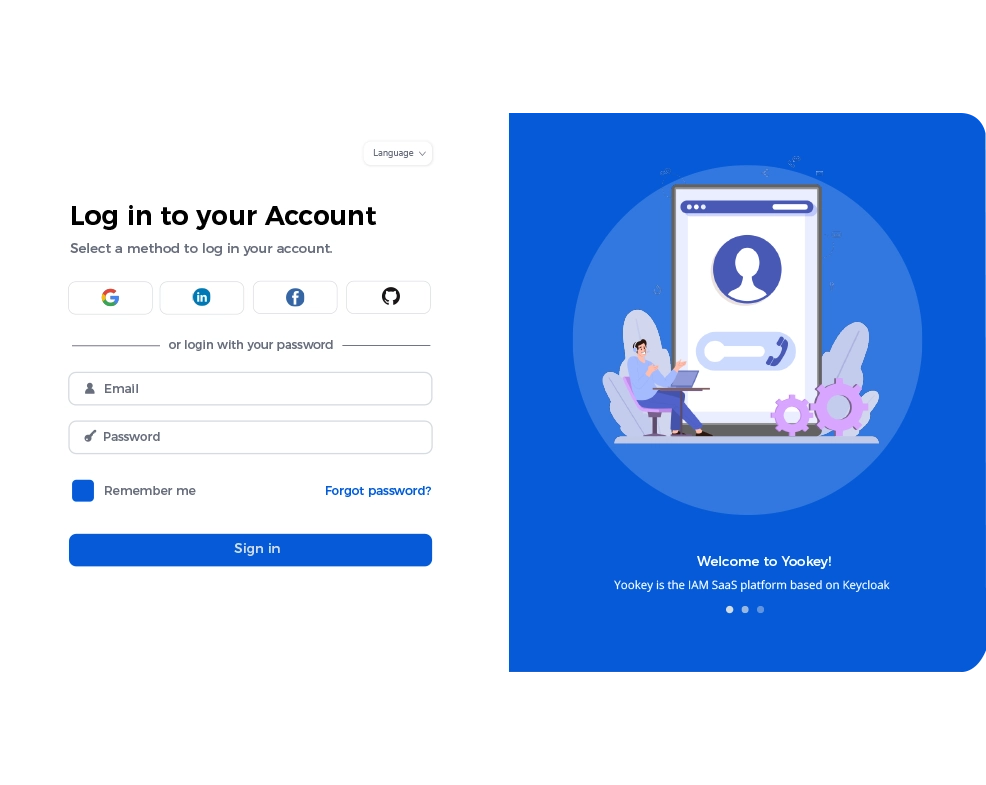
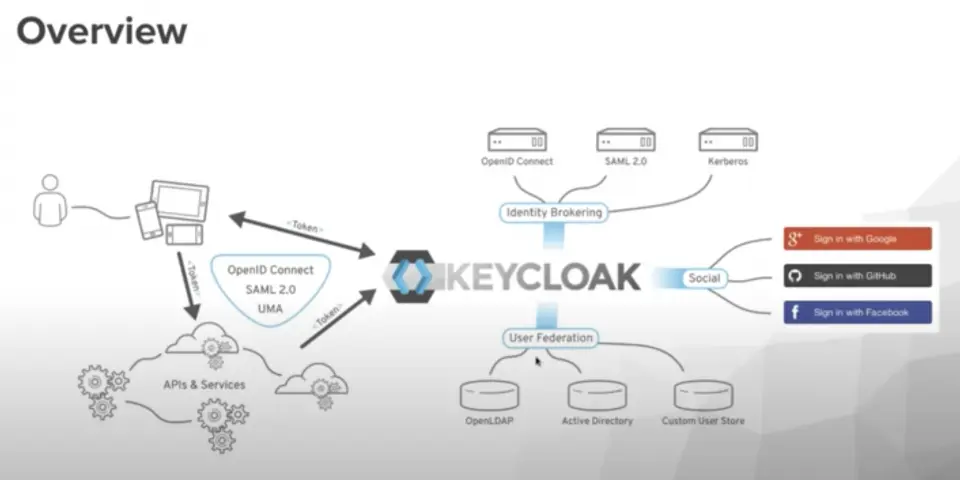
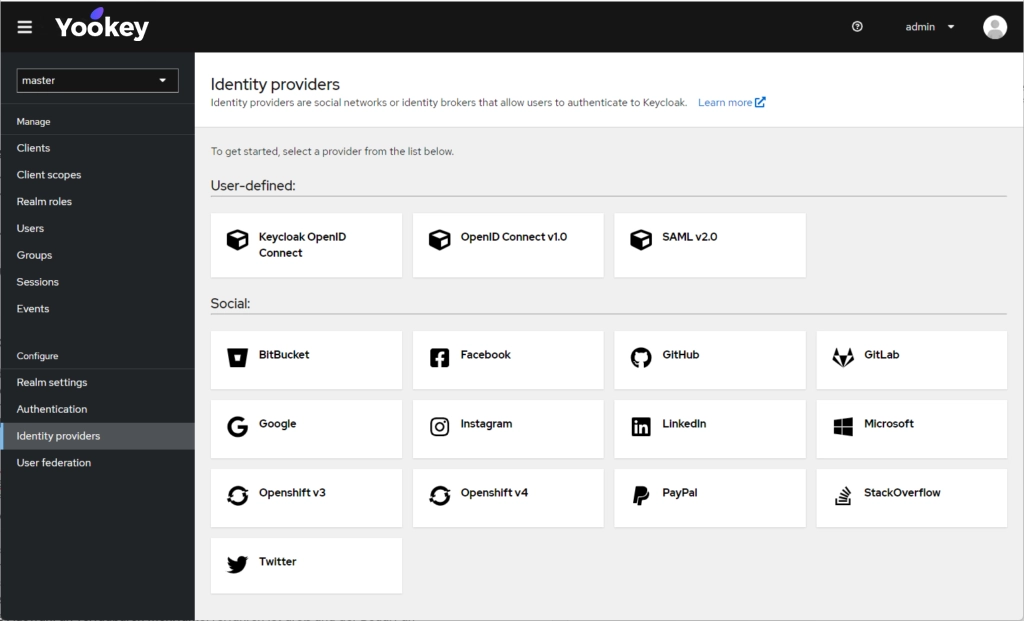
Yookey is a Keycloak-based Identity & Access Management (IAM) solution offered in SaaS mode, which centrally manages user authentication and authorization. It provides features such as Single Sign-On (SSO), multi-factor authentication (MFA) and support for standard federated protocols like OpenID Connect, OAuth2 and SAML v2.
Furthermore, Yookey allows integration with enterprise directories such as LDAP and Active Directory, as well as with national identity systems like SPID and CIE, ensuring security, regular updates, scalability and GDPR compliance.
Yookey applies RBAC by assigning permissions to roles for centralized management, granular security and compliance with company policies.
Speak directly with our team for more information.