Privileged Access Management (PAM) and IAM: Security and Access Control

What is PAM (Privileged Access Management) and How It works
Privileged Access Management (PAM) represents an advanced cybersecurity strategy designed to protect high-privilege accounts, i.e., those that provide access to an organization’s most critical resources. If compromised, these accounts can expose the entire IT infrastructure to serious risks.
For this reason, PAM governs and controls not only human administrator access but also access used by applications, automated services and IoT devices, which often communicate with each other using privileged credentials.
Next-generation PAM solutions offer advanced features such as session recording, detailed command monitoring and proactive blocking of potentially dangerous actions, such as unauthorized file transfers. In this way, PAM significantly reduces the risk of cybersecurity incidents and helps safeguard the organization’s entire IT ecosystem.
Difference between IAM and PAM: A direct comparison
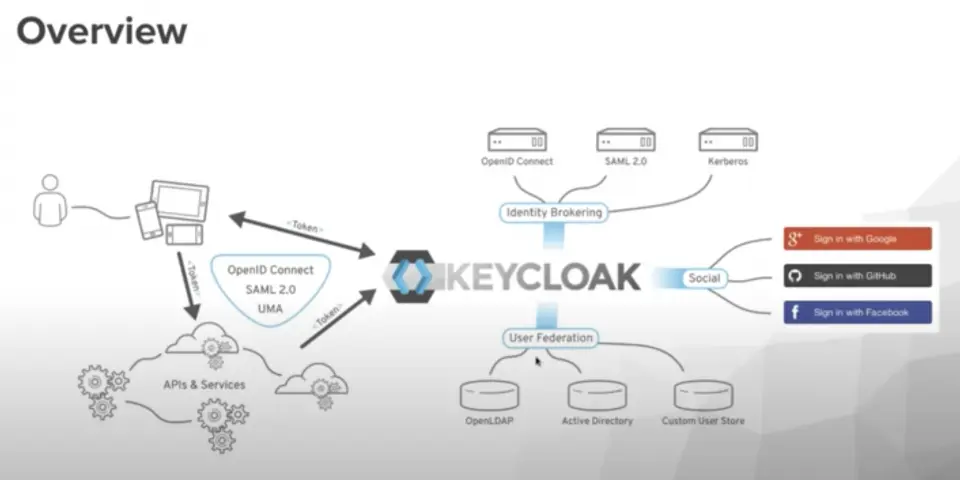
While IAM (Identity and Access Management) is designed to manage identities and access on a large scale, PAM operates at a deeper level, focusing on precise control and detailed monitoring of activities within critical systems.
The main differences between the two solutions become clear in several key areas:
- Scope of Application
IAM governs the daily access of employees, partners and customers to commonly used applications, such as corporate email, HR portals, and standard digital services. PAM, on the other hand, is exclusively dedicated to protecting high-risk access, such as access to servers, databases, and cloud infrastructures. - Level of Control
IAM focuses on identity verification at the point of authentication, ensuring that the user is authorized to access the system. PAM goes beyond the login: it supervises the entire operational session, monitors actions in real time, records activities, and allows immediate intervention to block anomalous or potentially harmful behavior.
Ready-Made Templates
Are you looking for an IAM system?Visit Yookey’s website to discover the available solutions.
When to use IAM and when to use PAM
The choice between IAM and PAM mainly depends on the type of users involved and the criticality level of the resources to be protected.
- When to Adopt IAM: IAM is the ideal solution for structured, large-scale management of digital identities. It is commonly used to automate the user lifecycle, such as onboarding, role changes, or offboarding, to implement Single Sign-On (SSO) and to regulate access to everyday corporate applications and standard business services.
- When to Adopt PAM: PAM comes into play when there is a need to increase security for the most sensitive assets. It is particularly suited to protecting access to critical IT infrastructure, managing shared administrative credentials and controlling third-party or vendor access, which often requires temporary permissions for technical support activities.
Integration between IAM and PAM: A Zero Trust approach
The combination of IAM and PAM represents a key element for building multi-layered security and effectively adopting a Zero Trust architecture. In this model, IAM serves as the first layer of verification, ensuring that the user’s identity is validated, often through multi-factor authentication (MFA), before granting access.
PAM, on the other hand, comes into play afterward by applying the principle of least privilege, restricting permissions strictly to what is necessary.
Thanks to this synergy, access to the most critical systems is controlled, monitored and time-bound. High-level privileges, granted only for limited periods are under constant supervision, significantly reducing the attack surface and preventing unauthorized movement within the IT infrastructure.
PAM and IAM as compliance tools
The implementation of IAM and PAM is often a fundamental requirement to pass compliance audits and ensure the security of critical systems.
In particular, PAM greatly simplifies this task by providing:
- Immutable audit trails to track every privileged activity;
- Video session recordings to verify administrator operations;
- Detailed reports on the use of high-privilege credentials.
Without a PAM system, reconstructing actions in the event of an incident or inspection becomes nearly impossible, increasing the risk of penalties or non-compliance with applicable regulations.
Yookey IAM Platform
Yookey, the IAM (Identity & Access Management) solution helps companies and organizations comply with major industry regulations, such as NIS2 and ISO 27001, by providing secure, efficient, and personalized access to digital resources.
With tools like Single Sign-On (SSO) and multi-factor authentication (MFA), Yookey enables fast and secure access to all platforms and digital services through a single login. Automated account and permission management ensures strict control over access to sensitive data and resources, guaranteeing full compliance with privacy and cybersecurity regulations.
Speak directly with our team for more information.